Cryptographic Key Generation
Advertisement
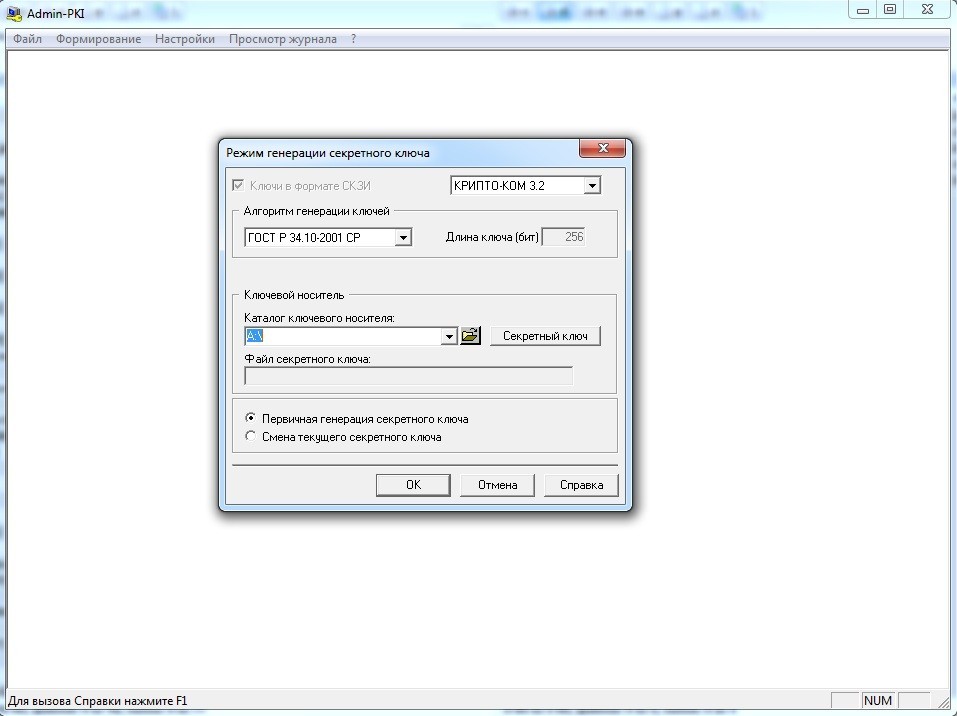
Admin-PKI v.4.1.0.10
Admin-PKI realizes the functions of the generation of cryptographic keys and certificate requests X.
Advertisement
A-Ware 2000 v.2.00
A-Ware 2000 is the share-ware author's total solution for customer tracking, software/program tracking, mass emailing and key-generation. Replace 6 software programs that you use now: Mail-Merge, Customer spreadsheet/database, knowledge Base,
VoiceCipher v.1 1
Use your voice as cryptographic key! VoiceCipher is file encryption software using strong cryptographic key created from your voice.
BasicCard Elliptic Curve PKS v.1.0
A smart card-based public key cryptography system based on elliptic curves, using AES for session key generation and SHA for hashing.
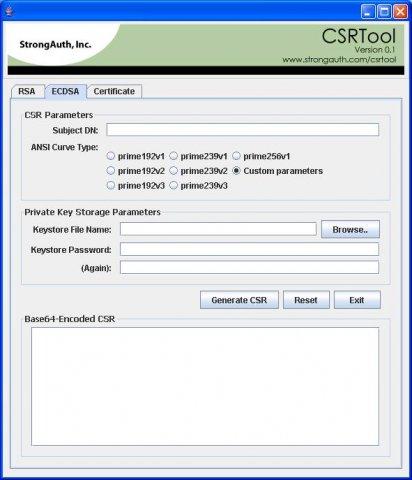
CSRTool v.29
A graphical tool for generating RSA and ECDSA cryptographic key-pairs, creating Certificate Signing Requests (CSRs) from them, and combining the key-pair with an issued digital certificate to create a secure portable container (PKCS12, JKS, JCEKS, et
Independent SecureSocketsLayer v.1.0
iSSL is a minimalistic cryptographical API that uses the ciphers RSA and AES to establish SSL-alike, secure encryptedcommunications between two peers communicating through a network socket, including session key generation and public key exchange.
JEasyORM v.0.9
Simple small extensible object relational mapper with database independent key generation and paging
System Key Wizard v.2 1
This is the best protection that you can ever place on the software that you develop at the best price ever. We have many happy customers in a variety of fields. One line of code to protect your investment that is all.
CrypTool v.1. 4. 1930
CrypTool is an open-source e-learning application, used in the implementation and analysis of cryptographic algorithms.
CryptoLab v.1. 2. 2002
CryptoLab is a freeware cryptography application for Microsoft Windows, and incorporates text-based encryption / decryption through the use of plug-in cipher modules.
Secure End-To-End Messenger v.1.0 Beta
Secure 2 peers chat/file transfer using Diffie-Hellman key exchange and DES/MD5 encryption. Can negotiate for a key for each message/file, utilizes a Diffie-Hellman Key exchange between 2 peers (one as server and the 2nd one as client). It uses RMI